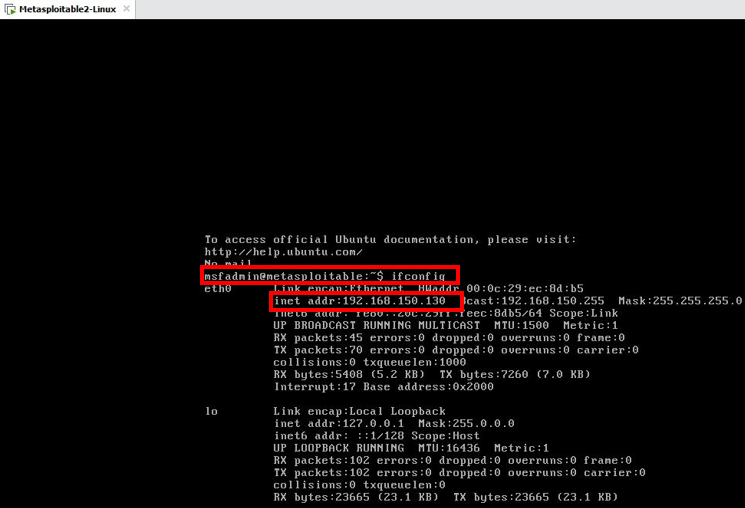
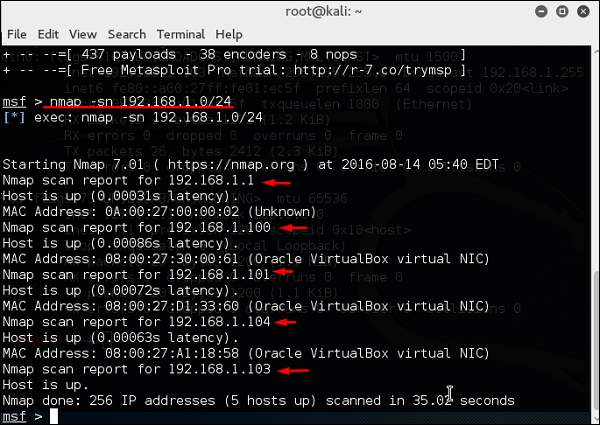
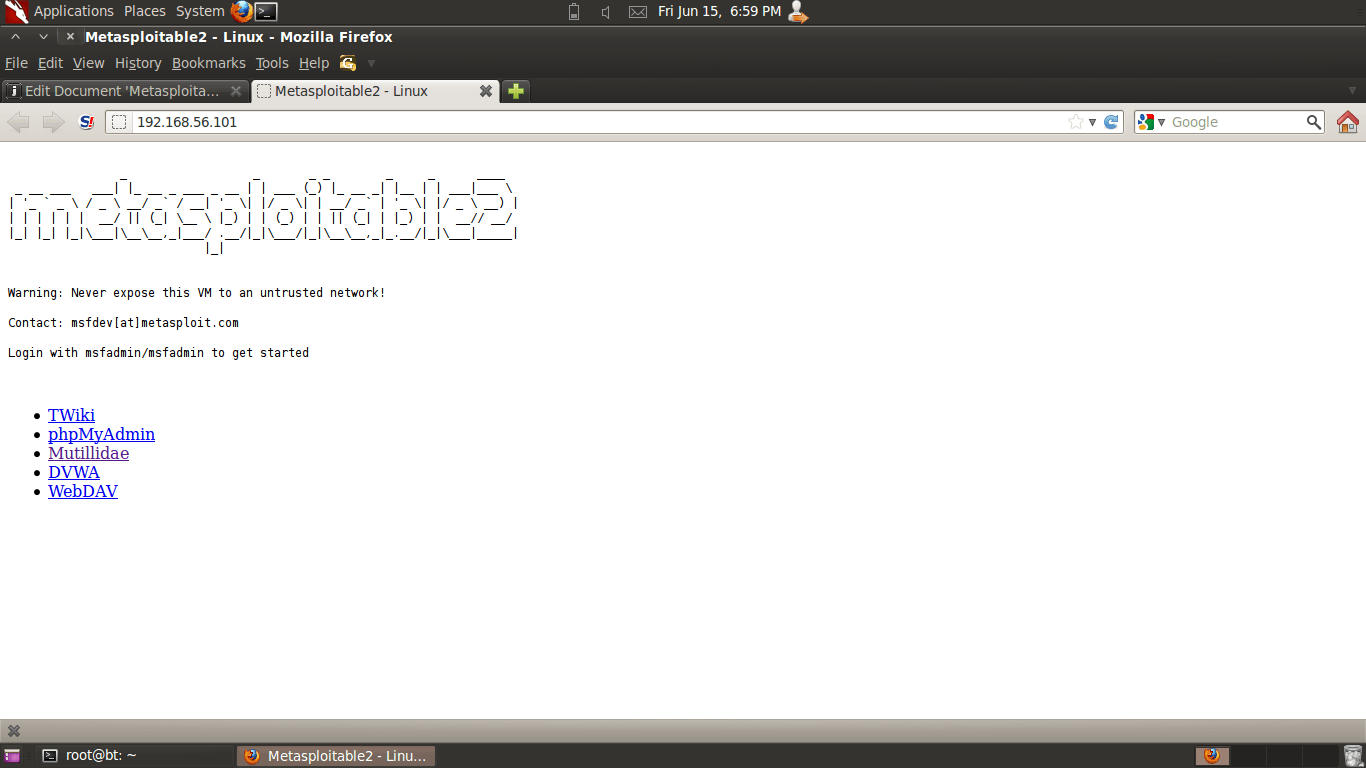
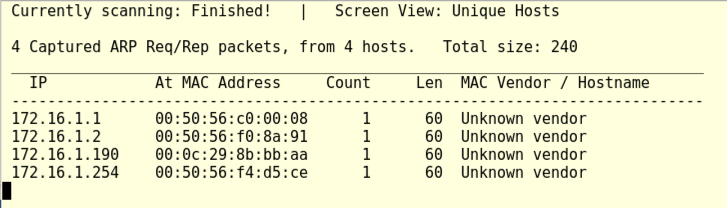
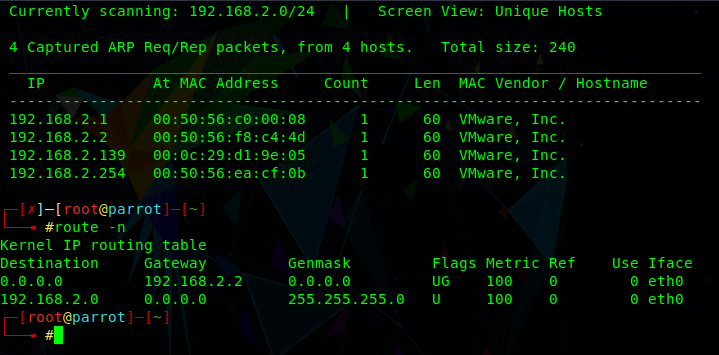
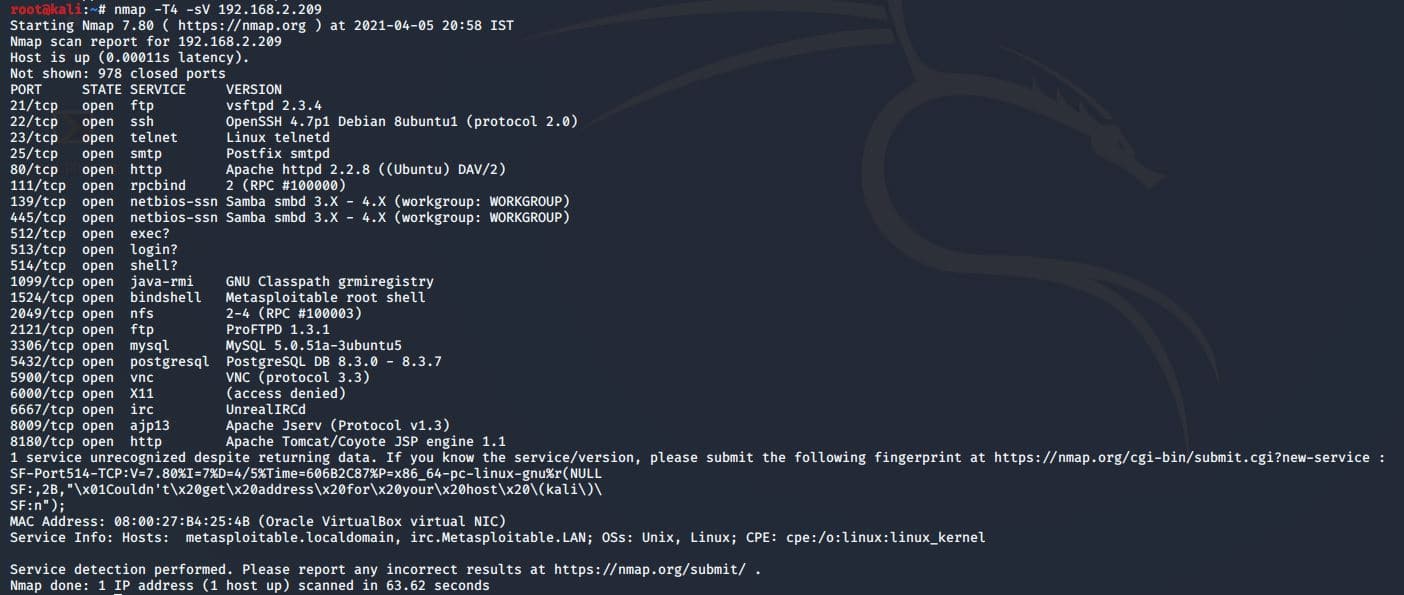
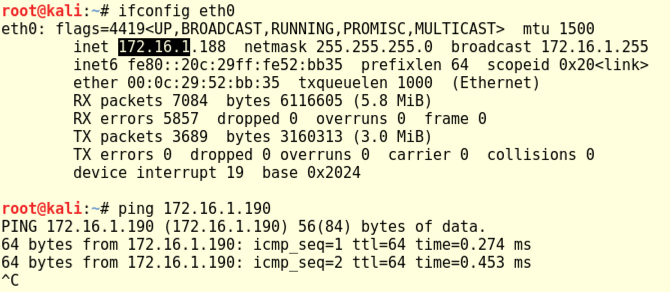
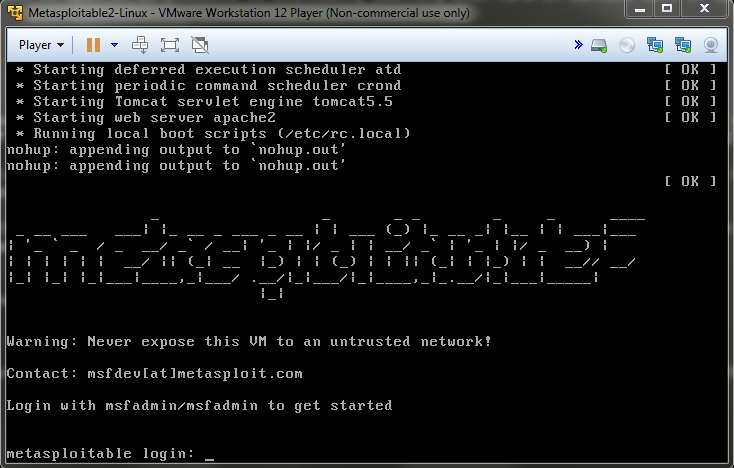
1 : FINDING IP ADDRESS AND SCANNING FOR OPEN AND CLOSED PORTS IN LINUX | METASPLOITABLE 2 | CTF - YouTube

windows - Kali Linux & Metasploitable VirtualBox VMs not getting IP addresses with Bridged adapter - Unix & Linux Stack Exchange

windows - Kali Linux & Metasploitable VirtualBox VMs not getting IP addresses with Bridged adapter - Unix & Linux Stack Exchange
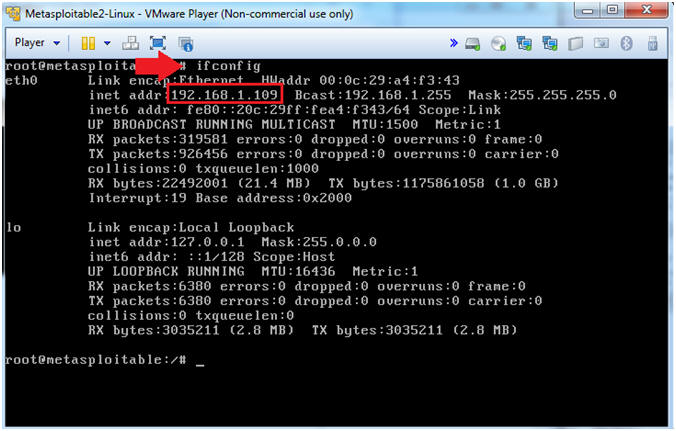
Metasploitable Project: Lesson 2: Exploit the distcc daemon to obtain root, Collect Lime Memory Dump


![Learn hacking with Metasploitable 2 [Step-by-Step] | GoLinuxCloud Learn hacking with Metasploitable 2 [Step-by-Step] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/kali-1.jpg)